Which Type of Proxies worth to Buy? Read our Ultimate Proxy Comparisons to help you find the best proxy sites to match your Online marketing, Security and Privacy requirement.
For those who aren’t aware, a proxy or proxy server is essentially another computer or server which processes commands and requests around the web. Your computer will send its requests to the proxy server and in return, the proxy will provide you with what you want.
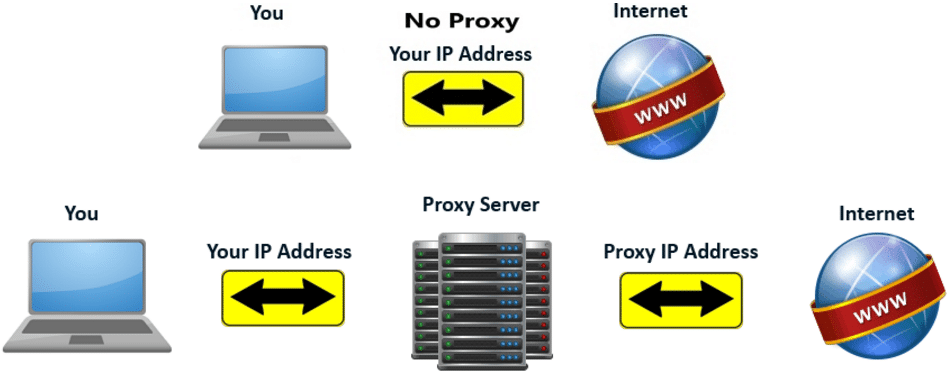
Basically, a proxy server acts as a mediator between your computer and the rest of the computers on the internet, And with this image you can easily know “How the Proxy Server works.”
Ultimate Proxy Comparisons
Table of Contents
Now more and more Free Web Proxy, Dedicated Proxy, Backconnect Proxy, IP:Port Proxy and more come to the market. There are many proxy services available, Some of the proxies are free, some of the proxies are paid, you may want to find a proxy with reasonable price. but really difficult to determine which is the best proxy service available for your needs.
Skip the long-time research to find the proxy online. I have researched and used virtually on all of the most popular proxies, No more Complex theory, I will show you the best proxy sites on your purpose and Compare the different type of proxies for you in an easy way. So, before anything else, let’s take a look quickly at the Proxy Comparisons Table.
| Tpye of Proxy | Cost | IP Address | Protocol | Speed | Privacy Levels |
|---|---|---|---|---|---|
| Backconnct Proxy | Paid | Residential IPs | SOCKS /HTTP(s) |  |  |
| Private Proxy | Paid | Data center IPs | SOCKS /HTTP(s) |  |  |
| Shared Proxy | Paid | Data center IPs | SOCKS /HTTP(s) |  |  |
| Public IP:Port Proxy | Free | Mixed IPs | SOCKS /HTTP(s) |  |  |
| Web Proxy | Free | Data center IPs | Glype/PHP/CGIProxy |  |  |
| VPN | Paid | Data center IPs | PPTP/OpenVPN/L2TP |  |  |
| Tor | Free | Residential IPs | Tor |  |  |
Now let’s continue to the detailed of different types of Proxy. Here I will add the most popular proxy servers which are the highest performing choices.
Backconnect Proxy
Backconnect Proxies are also known as rotating proxies or rotating Reverse Proxies. This type of proxy mainly used for commercial scraping or crawling projects. It’s another type of IP address solutions to change requests from different IP address every 5 minutes or 10 minutes.
Backconnect Proxy service usually runs P2P routing network, such as Luminati offer free VPN service named Hola, The P2P network offers a vast quantity of Residential IPs as proxy servers.
Read more, How Luminati Residential Proxies works?
The Backconnect Proxy allows users to send their requests through users of the P2P proxy network. It’s behind single IP gateway (Port), When you get 10 ports or 10 proxies of Backconnect Proxy, your IP address can rotate to huge amounts of different IPs which in the P2P proxy network.
- Web crawling & scraping tools to avoid IP ban
- SEO tools, like Scrapebox, GSA search engine ranker, RankerX, and so on
- Mass Accounts Creation and Registration
- Using on Sneaker sites, Traffic bots and more…
- Speed is slow compared with a dedicated proxy
- Not good for browsing
- Connection is unstable
Best Backconnect rotating Proxy Providers 2024
Here is another post to help you to know more about Datacenter proxies or Residental proxies for copping the sneaker?
Private Proxy
There is no doubt that a private proxy is one of the best types of datacenter proxy online, lots of proxy sellers would like to call it dedicated IP proxies.
A private proxy is exactly what it sounds like, a dedicated proxy server that is only accessible by one individual and nobody else can use this proxy.
Using a dedicated proxy has the benefit of not being subject to the possible consequences of other peoples’ actions, and in most cases, they are significantly faster as they aren’t affected by user congestion, as only one individual is using the server.
Compare the open proxies with private proxies, One difference is that private proxy is needed to authorize to use. Generally, after you buy the proxy service, you may get the proxy like,
IP:PORT:Username:Password
Also, some of the private proxy providers offer IP authentication, So you get the proxy lists as IP:PORT, but you need to authorize your IP on their client area first.
- Speed of Dedicated Proxy is Really Fast
- Private Proxies good for Scraping
- Dedicated Proxies are good for Sneaker Bots such as AioBot
- Proxies to manage Social Media account, such as Private Proxies for Instagram
- Unblock IP address Censorship such as on, Craigslist and Ticketmaster
- Good for Anonymous surfing and Unblock Geographic restrictions
- Cost – usually $2/Month per IP
- IPv4 exhaustion (More and more hard to find fresh IP address)
Best Private Proxies providers 2024
The Key is the IP address that’s exclusive and fixed, You’ve fully supervised this IP, Don’t worry about the IP address be abused by others. That’s why lots of internet marketers like to use private proxies for their tasks, such as Data scraping or copping shoes.
Shared Proxies are exactly what they sound like: a proxy server that is shared by several users, But it’s not open proxies, it’s also provided by the proxy service and has similar benefits and limitations to that of regular private proxy servers.
Shared Proxy also called Semi-dedicated proxy, the different with private proxy is the proxy is shared to use by other paid clients, so it’s cheap than private proxies.
- Fast Speed (than VPN)
- Works great on SEO tools such as Scrapebox, GSA search engine ranker
- Cheaper than private proxies
- The IP address may be banned by other users
- Shared proxies mainly recycled IPs
- Not Good for footsites and ticketing sites
But the IP address is shared by other clients, which means the IP address of shared proxy can not just control by you. So, If you need fresh IP, Shared proxies, not a good option.
Free Public IP:Port Proxy
The Open Proxies are known as Free Public IP:Port Proxies, from the name you may know, this type of proxies can be easily found online. There are millions and millions of public proxy servers on the web for different purposes. You may don’t know What’s the IP address and Port meaning? Let me show you the detail.
A proxy show as IP:Port, such as,
192.99.79.159:8080
If a home Computer or dedicated server (or VPS) want to on the internet, the IP address -192.99.79.159 is assigned a by ISP. Then if the Computer or server wants to act as a proxy server, Then you have to install a proxy program(such as Squid) which runs on the Computer or dedicated server, the program lets the server run as Proxy Server on port 8080. Usually HTTP Proxy runs on port 8080 and 80.
- Change your IP address to Specific country or subnet
- Choose the Proxy Protocol (SOCKS or HTTP) as you want
- Can be run on SEO software to Scrape and Post
- Proxy die fast! Really Time Consuming
- Not good for browsing
- Really Not Safe
- Don’t use it on financial or Social networking sites
Free Public IP:Port Proxy Sites
The public IP: Port Proxy Sites are run proxy harvesting script on their server to constantly scan public proxy server online, after harvesting the proxies then check the proxy speed, response time, Anonymity levels, Protocol and so on. After checked the proxies, the server print the proxy server list as IP:Port list. And You can easily find the free proxy list online, Here the 5 best proxy list sites which is popular to use.
| Rank | Public IP:Port Proxy Sites | Link |
|---|---|---|
| 1 |  | https://hidemy.name/en/proxy-list/ |
| 2 |  | https://www.proxynova.com/proxy-server-list/ |
| 3 |  | https://proxy-list.org |
| 4 |  | http://list.proxylistplus.com/ |
| 5 |  | http://freeproxylists.net/ |
But the free public proxy lists are easy to detect and really unreliable, Just thinking this, When hundred of persons or Bots use this proxy server, The speed and bandwidth are shared to all users!! So, don’t ask me the speed fast or not. You should have the answer, Not to mention the IP address virgin or fresh.
Web Proxy
The Web Proxy is the easiest to use a proxy server. The Web Proxy just a website act as a proxy server, when you access a web-based proxy, easily enter the URL you’re want to visit you can connect to the website. If you are puzzled about web-based proxy, Don’t forget to have a look at the “Ultimate Guide on Web Proxy“.
- Bypass Internet Censorship
- Unblock Website in School for Free
- Anonymous Surfing
- Speed is Really Slow for It’s Free
- Only for Browsing
- Not Safe
Best Free Web Proxy 2024
There are so many web proxies online, 99% of web proxy sites are free to use. However, I always believe in “Thing marked free, costs extreme.” The free proxy websites are full of advertisements. Even worse, There may be Trojan or Malware on the proxy sites! So, you have to be careful about it, here is a list of Top 5 web-based proxy websites I recommend to you.
VPN Service
VPN means the virtual private network that allows you to hide your IP address and geographical location by tunneling your entire internet connection through another server (Proxy only works on the HTTP/SOCKS protocol, that’s means proxy only tunnel the traffic on special application, such as browsers).
Related: How to use a proxy in Chrome, Firefox, IE, Microsoft Edge, and Safari
The VPN tunnel is encrypted. This tunnel is connected to a dedicated VPN server, and it appears as if all the browsing is being done on the VPN server itself.
This not only provides you with privacy, security, and anonymity when surfing the web but also allows you to gain access to restricted websites and allows you to bypass certain filters.
- Unblock Restricted Websites
- Protect your Wi-Fi connection
- Blazing Fast internet connection for browsing
- Encrypt internet traffic for online privacy
- VPN service is more expensive than proxy
- IP address of VPN server is shared
Best VPN service 2024
And the VPN service offer lots of server locations that’s you can use, and speeds and IPs of the server are shared to all their clients, there is a shortcoming that’s if you need a lot of dedicated IPs for Internet Marketing or SEO industries.
Tor Network
TOR stands for The Onion Router and is essentially a series of virtual tunnels that act similarly to a proxy server. The difference is instead of your connection being pasted through just one computer, your connection is bounced through several computers, creating layered protection. Hence why it’s called ‘the Onion Router’.
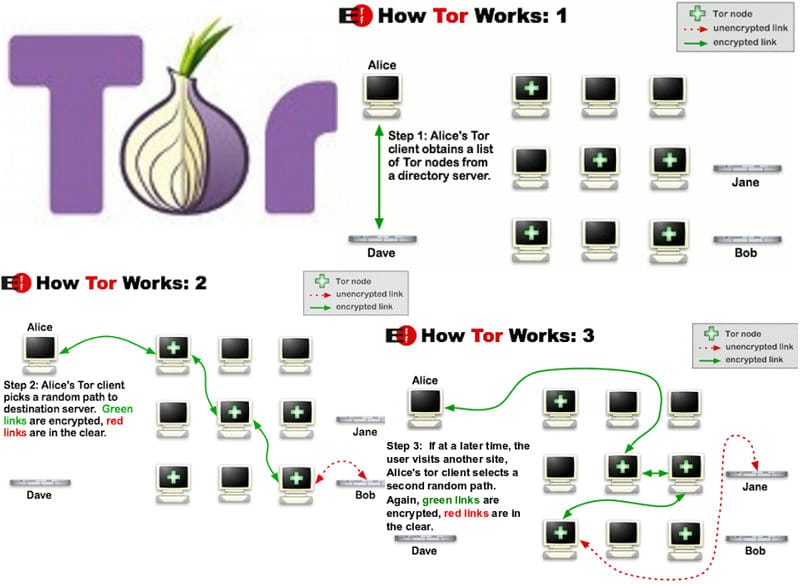
As your connection is passed through different computers, your IP address if hidden and your geographical location is hidden also. The computers who are involved in the process are known as TOR relays and there are three types: middle relays, end relays, and bridges. The initial connections are all encrypted and the final connection is not as it is usually considered to be ‘in the clear’.
- Good for anonymous browsing
- Slow!!
Conclusion
All the proxy services or proxy sites added on stupidproxy.com, We all have tested then added on this page to help you find the best proxies to Meet your anonymous or marketing needs.
And there are lots of types of proxy servers and all of the proxies provide by the proxy service which should be named as the Forward Proxy servers.
If you’re want to know the basics about what is the proxy and different between Forward Proxy and Reverse Proxy, We just write an Ultimate Guide to Proxy Servers, Which also introduced about HTTP Proxy, Socks Proxy, Data Center IP Proxy, Residential IP Proxy, DNS Proxy and more.




























